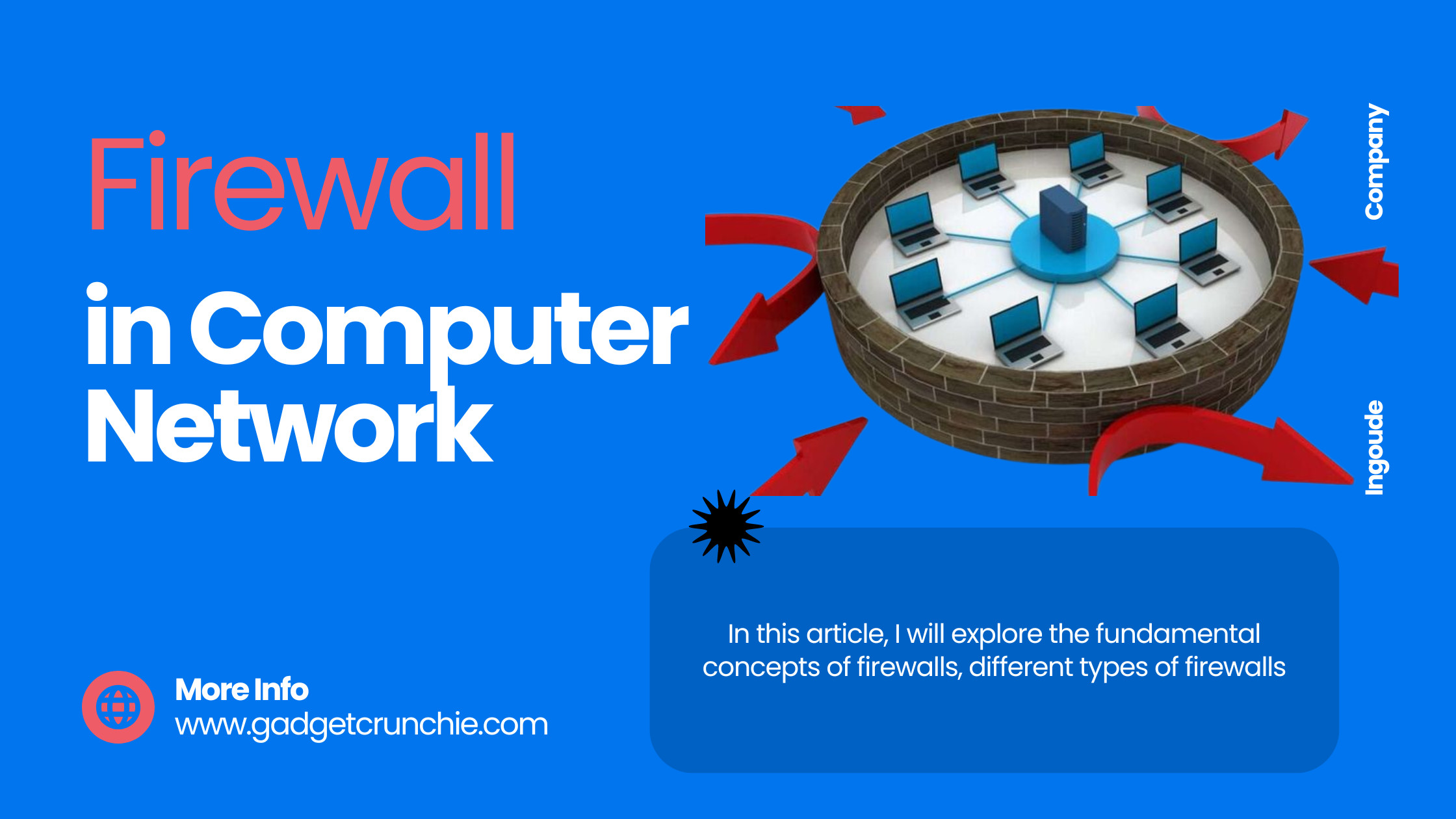
Firewalls play a crucial role in safeguarding computer networks from various cyber threats by acting as a barrier between trusted internal systems and untrusted external networks. Understanding the introduction of firewalls in computer networks is essential for ensuring the security and integrity of digital information. In this article, we will explore the fundamental concepts of firewalls, different types of firewalls, their functions and benefits, as well as best practices for their implementation and management. Additionally, we will discuss common firewall configurations, monitoring and maintenance strategies, and delve into future trends shaping firewall technology in the ever-evolving landscape of cybersecurity.
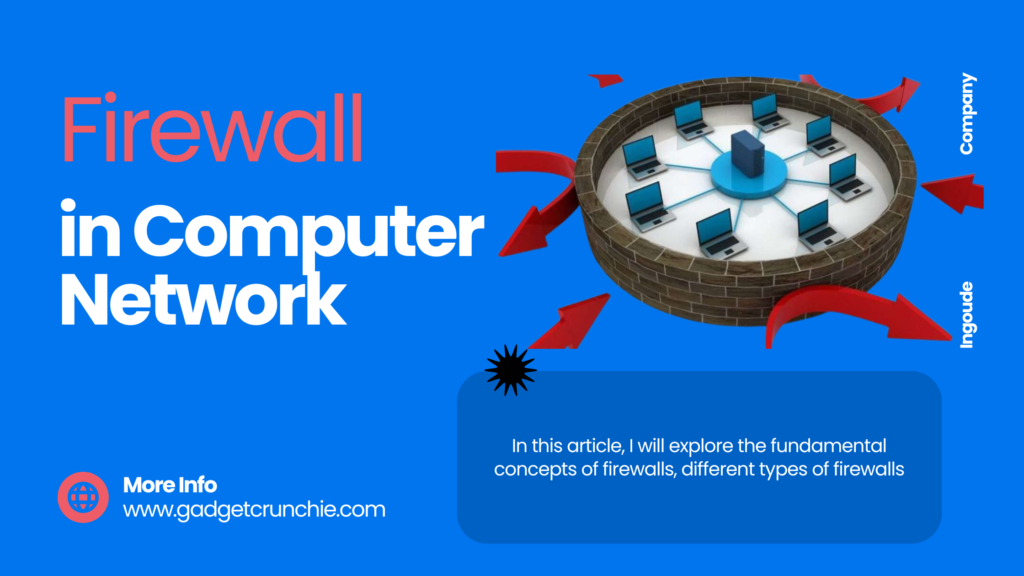
Overview of Firewalls
Firewalls are like the bouncers of the digital world, standing guard at the entrance of your computer network to keep out unwanted guests. They act as a barrier between your internal network and the wild, wild web.
Definition of a Firewall
A firewall is a security system designed to monitor and control incoming and outgoing network traffic based on predetermined security rules. Think of it as the gatekeeper that decides who gets in and who gets blocked.
Historical Evolution of Firewalls
Firewalls have come a long way since their inception in the late 1980s. From simple packet filtering to more sophisticated proxy and stateful inspection techniques, firewalls have evolved to keep up with the ever-changing landscape of cybersecurity threats.
Types of Firewalls
Just like there are different flavors of ice cream, there are also different types of firewalls to suit your network’s security needs.
Packet Filtering Firewalls
Packet filtering firewalls work by analyzing individual data packets entering or leaving the network and deciding whether to allow or block them based on specific criteria. It’s like sorting through your mail and tossing out the junk.
Proxy Firewalls
Proxy firewalls act as intermediaries between internal and external network traffic. They fetch data on behalf of users, adding an extra layer of security by masking the internal network’s IP addresses. It’s like having a secret agent to handle your web requests.
Stateful Inspection Firewalls
Stateful inspection firewalls combine the best of both worlds by keeping track of the state of active connections and making decisions based on the context of the traffic. It’s like having a firewall that’s not only smart but also has a good memory.
Functions and Benefits of Firewalls
Firewalls aren’t just there to rain on your network’s parade. They serve some crucial functions and bring a whole bunch of benefits to the cybersecurity table.
Protecting Against Unauthorized Access
By setting up rules and policies, firewalls act as the gatekeepers of your network, preventing unauthorized users or malicious software from sneaking in and wreaking havoc. It’s like having a bouncer at the club entrance checking IDs.
Monitoring and Controlling Network Traffic
Firewalls keep a watchful eye on the traffic flowing in and out of your network, allowing you to monitor and control what data is allowed to pass through. It’s like having a traffic cop directing the flow to prevent gridlock.
Firewall Implementation in Computer Networks
Now that you’re familiar with the different types and benefits of firewalls, let’s talk about how to bring them into the fold of your computer network.
Placement of Firewalls in Network Architecture
Deciding where to place your firewall in the network architecture is crucial. Whether it’s at the network perimeter, between internal network segments, or within individual devices, the placement can impact the level of security provided.
Configuring Firewall Rules and Policies
Configuring firewall rules and policies involves defining what traffic is allowed or blocked based on specific criteria. It’s like setting up your own security guidelines to ensure that your network remains safe and sound.
Common Firewall Configurations
Single vs. Dual Firewall Setup
When it comes to safeguarding your digital perimeter, deciding between a single or dual firewall setup is crucial. A single firewall provides a layer of defense between your internal network and the internet. On the other hand, a dual firewall configuration involves two separate firewalls in sequence, adding an extra layer of protection. Think of it as having one guard at the gate versus having a bouncer checking IDs before the guard lets you in.
Host-based vs. Network-based Firewalls
Understanding the difference between host-based and network-based firewalls can help tailor your defense strategy. Host-based firewalls are installed directly on individual devices, controlling traffic to and from that specific device. Meanwhile, network-based firewalls protect an entire network by filtering traffic between the network and external sources. It’s like having a bouncer at each club entrance versus a bouncer at the gate of the entire party.
Best Practices for Firewall Management
Regular Firewall Auditing and Rule Review
Just like cleaning out your closet, regular firewall audits and rule reviews are essential for maintaining an effective defense. By checking and updating firewall rules, you can ensure that only authorized traffic is allowed in and out. It’s like decluttering your network to keep things running smoothly and securely.
Implementing Intrusion Detection and Prevention Systems (IDPS)
Adding an Intrusion Detection and Prevention System (IDPS) to your firewall setup is like having a security guard who not only checks IDs but also knows when to kick out troublemakers. IDPS monitors network traffic for suspicious activity and can automatically take action to block potential threats. It’s like having an extra set of eyes and muscles to protect your digital fortress.
Monitoring and Maintaining Firewalls
Logging and Analyzing Firewall Events
Logging and analyzing firewall events is like having a security camera in your network, capturing and documenting every suspicious move. By keeping detailed logs and analyzing events, you can spot patterns, identify potential threats, and take proactive measures to strengthen your defenses.
Updating Firewall Software and Firmware
Regularly updating firewall software and firmware is like getting the latest security patches for your castle walls. These updates often include bug fixes, vulnerability patches, and new security features to keep your firewall robust and up to date against evolving threats.
Future Trends in Firewall Technology
Integration of Artificial Intelligence and Machine Learning
The future of firewall technology is embracing Artificial Intelligence (AI) and Machine Learning (ML) to enhance threat detection and response. By leveraging AI and ML algorithms, firewalls can adapt and learn from patterns of behavior to detect and mitigate emerging threats in real-time. It’s like having a self-learning guard dog that can anticipate and defend against new tricks from intruders.
Enhancements in Cloud-based Firewall Solutions
Cloud-based firewall solutions are shaping the future of network security by providing scalable and flexible protection for modern digital environments. These solutions offer centralized management, seamless scalability, and enhanced threat intelligence, making them ideal for securing cloud infrastructure and distributed networks. It’s like having a virtual security team that can adapt and expand with your digital footprint, ensuring robust protection wherever your data roams.
Conclusion
In conclusion, the introduction of firewalls in computer networks is a critical component of modern cybersecurity strategies. By implementing and managing firewalls effectively, organizations can enhance their network security, protect sensitive data, and mitigate potential cyber threats. As technology advances and cyber threats evolve, staying informed about the latest trends in firewall technology will be vital for maintaining a secure digital environment. With a solid understanding of firewalls and their role in network security, organizations can fortify their defenses and safeguard against cyber attacks in an increasingly interconnected world.